An amazing bit of digital detective work here. Seems like Linux mobile is your only off ramp from being exhaustively tracked
That’s crazy. As it’s (almost) impossible to prevent those data to be sent from the phone, would it be possible to make the data useless ? For instance by sending loads of fake json payloads for some ids ? Then enjoy my data which says at the same time that I’m in Vancouver, Lisbon, Paris, on my low cost and super expensive phone, with volume at max and zero,… Not possible I guess ?
Surprising that this data never heard gets leaked. It’s always my social security number
It’s in a perpetual state of leakage in a sence that it’s a trade item that gets sold between different companies. You can’t leak that, really.
Does this happen to users in the EU? It’s highly illegal to gather data without consent here obviously. Even processing other data to derive location (which is personally identifiable information) means processing data for purpose that’s different to one that was consented to (if they tried to get any consent at all). There are big companies implicated here so it’d be easy to fine them into submission in jurisdictions that allow it.
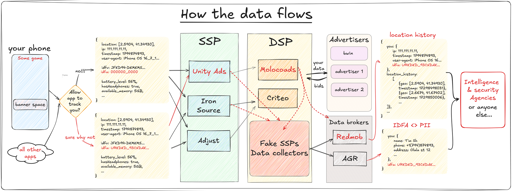
The sample data shared in the article includes
"c": "ES", // Country code,ES is usually used for Spain, so it looks like these tests were run from within the EU.
Ah, there’s also this piece in json:
"uc": "1", // User consent for tracking = True; OK what ?!My guess is that developers are pretending to get user consent to get more money from the ads. Unity could be encouraging this somehow but good luck proving that.
Easier to ask forgiveness than permission. Most companies are so big, getting caught is relatively cheap with how low the fines are compared to their annual profits.
It’s just a line item on their expense sheets, anymore, and most people don’t have the money to get the justice they deserve in court.
This we can expect but there’s also a trend to idolise solo developers or small firms. Reality is that everyone can be shitty and therefore everyone should be accountable. In this case a smaller developer steals user data do defraud Unity most likely because they think they’re too small to be worth investigating. When we were implementing GDPR in my country those small developers fought this law as oppressive and unnecessary.
it’s been known for a long time that there is enough identifiable information in a “normal” person’s internet usage to identify exactly who and where you are and what you are likely doing just from metadata analysis and public domain information
question is, how is this being abused
All HTTP requests include your ip address, you don’t “consent” to giving it to anybody. You can geolocate somebody based on ip address but it won’t be very accurate
True, it’s storing the IP address that is the issue.
Storing it and associating it with all the other identifying information collected.
but it won’t be very accurate
Which they actually acknowledge in the blog post.
Kind of interesting that they’re smart enough to understand how to sniff packets but not enough to understand that IP address = location.
Author noted:
As a quick note - location shared was not very precise (but still in the same postal index), I guess due to the fact that iPhone was connected to WiFi and had no SIM installed. If it was LTE, I bet the lat/lon would be much more precise.
And this was with location services off. How precise is a “postal index” in the author’s country (presumably Spain) I wonder.
Use a VPN. Problem solved.
Latitude and Longitude are in there. As is screen brightness. He does acknowledge that he is on Wi-Fi, but that’s still super suspicious
Using a VPN just moves the trust to another middleman.
Multiple middlemen are better than just one. Also, you can test its effectiveness.
Yeah, a middleman you get to choose. That’s a huge improvement. There are plenty of trustworthy VPN providers.
So use a trustworthy middleman? Surely you can find someone more trustworthy than advertising companies?
You can set up wireguard vpn on a tiny instance in Amazon or Google, and bounce traffic through that one. Then you control what gets logged (Amazon may have logs over all outgoing connections from all instances somewhere though).
You can even make it change it’s public ip every day if you want.
Tor over VPN
Is that tinfoil hat comfortable?
Using a VPN means that all your traffic is routed through a possibly malicious actor.
Like Kevin Spacey?
That’s gold, Jerry!
This problem solved, but whenever you change your network or IP and then periodically, your phone will report to Firebase, so you can receive push notifications.
You can block those with software that simulates a local VPN with a filter, but you won’t get any more push notifications. Now push notifications are not just the ones you see. Some apps use invisible ones to get infos they need to work.
But when Firebase gets that network/IP change report, what information does it get? Because if it only gets the public IP address, the reported IP will still be the VPN one, not the real one, right? So, if that were the only information reported to Firebase, wouldn’t you still be protected? Does Firebase block requests when you’re using a VPN (this could be detected, for example, if certain aspects of the network have changed but the IP hasn’t)? Is that what you mean with not getting push notifications when simulating a local IP with filters?
PS: From my research, the WiFi’s SSID can also be used to track someone’s whereabouts, but depending on where you are and how many networks have used the same SSID, it may work work well or badly. You can see that by going to https://wigle.net/ (which is a database on WiFi networks with some publicly-available information), go to the map, type in the SSID field, and click “Filter”. I’m not sure if Firebase gets that info in the network reports, but I find it likely that it does.
It gets your unique tracking ID, so it knows you’re the same person now with different IP. If you use apps that store location data in firebase (eg. find my device, fitness trackers, emergency alert apps) it will upload your GPS location and maybe nearby wifi names, if you set it to be extra precise.
Make sure you disable or properly configure webrtc. Even with a VPN it will leak your true IP address.
Check here.
Not the magic bullet people think they are. Oh, and you can’t turn it off, so you’ll have to take the loss in network speed on absolutely everything. And better know how to configure each device so it doesn’t go ahead and check leak your IP anyways, which also restricts choice of devices you use. Cause remember, if any device on your network ever connects to the net without the VPN, then your anonymity just went out the window.
Not the magic bullet people think they are.
No one thinks VPNs are “magic bullets”. I don’t know why this gets repeated ad nauseum.
Oh, and you can’t turn it off, so you’ll have to take the loss in network speed on absolutely everything.
True but it’s not that bad.
And better know how to configure each device so it doesn’t go ahead and check leak your IP anyways
Just choose a good provider. You don’t need to configure anything.
if any device on your network ever connects to the net without the VPN, then your anonymity just went out the window.
That’s what kill switches are for.
No one thinks VPNs are “magic bullets”. I don’t know why this gets repeated ad nauseum.
Ooh, I know why! It’s because YouTubers hawk their preferred (sponsored) VPN as if it was silver bullet and that it’s dangerous to use your mobile device out in public or worse – public WiFi – without it. You can’t blame John or Jane Doe from parroting what their favourite YouTuber claimed.
I agree it’s a powerful tool! I was specifically responding to “problem solved” in the previous comment. My reply was in no way meant as a general review of VPNs.
That VPN provider will then know ALL the connections you make. Almost worse than just using the Internet normally.
That’s an uninformed statement.
You get to pick your provider. So pick one that you trust.
It’s FAR better than without as your ISP is probably selling your traffic to third parties or at least monitoring it. Some VPNs don’t.
Even with Linux it wouldn’t be that safe, if apps were doing this crap.
You’d want to be using only Linux apps that weren’t recording and reporting everything. Much easier to get in Linux than Apple/android
You know the towers log data too, right? And that websites themselves can track you regardless of what OS you use, right?
Privacy is good, but stop with this “Linux is a magic weapon” BS.
Separate dongle for internet using a hotspot can help. No system is perfect but Linux phone is an excellent first step
You miss my meaning. All the servers that your info passes through, all the cell towers, etc, can and in many cases do track you(even as just routine loggings). Thinking that running anything makes you more secure while connecting to a giant public network is naive.
We just have to stop using the internet at this point
Is there any straightforward way of stopping this besides dropping off the grid?
Use a custom DNS and/or hosts file. You can cut them off the grid by blocking data upload to SSP. Don’t install many apps, for games that can be played offline, play them offline. EDIT: AdGuard DNS doesn’t block the 1st URL (o.isx…) in the page. 2nd URL is blocked.
Using firefox in strict mode with ublock origin, cookie auto-delete, and a VPN to change your IP every now and then should stop location tracking and cross-site tracking. Sites will still know you’ve visited them and what pages you’ve been to in that session, but that is impossible to stop.
The main thing is don’t use apps, they can collect tons of data and tie it directly to your physical device, and run in the background while not actively using it.
Using a web browser is really the safest option I can think of because you have control over almost everything.
Route all or traffic through tor. Never log into anything. Never use the same identity twice. Ahh and live in a hut in the woods never going to shops or cities that have security cameras.
I think it’s more: “Don’t use a smartphone”. It’ll send those requests through any internet connection. No matter if it’s a VPN or Tor.
Google hardcodes DNS into their hardware appliances…
So you’d need to block outgoing DNS requests except for your DNS server and god forbid you change location with a smartphone.I think this is about apps and not the operating system. But yeah, the stock ROMs also phone home to Google. You’d need to patch that. For example like custom ROMs like GrapheneOS do. I don’t see another viable alternative. But that still leaves you with the issues with the apps mentioned in the article.
I forgot I’m in a minority of people running a properly secure degoogled ROM.
Same, same. But the occasional app refusing to work due to missing Play services, all the Instagram posts everyone except me took notice of, and all the hoops I have to jump through, kind of remind me of that regularly.
…where are chains allowed to abuse security camera footage for ad tracking?
Bunnings in Australia until very recently and u have basically 0 protections in the states.
I imagine an ad blocker could prevent this data going out, unless the hosts were generic and the game/app simply won’t work without allowing those connections. I’ve never seen an app be [obviously] broken from my ad blocker but I am interested in running a similar experiment to see just how much data is going out.
None worth pursuing
Wonder how the app sent geolocation with Location Services disabled.
It may have estimated location data with IP from Wi-Fi. Location Services turns on GPS but that is not the only way of getting location.